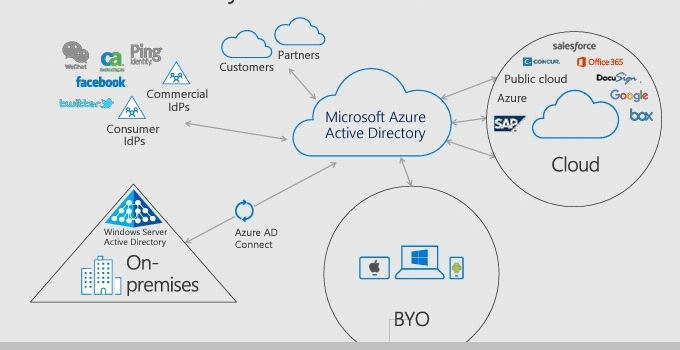
Azure AD identity and access management enable deep security, productivity, and management across devices, data, apps, and infrastructure. It’s an integral
Modern Workplace | Cloud Computing | Cyber Security


Azure AD identity and access management enable deep security, productivity, and management across devices, data, apps, and infrastructure. It’s an integral
Cyber threats are emerging more frequently and prevalently and to protect your organisation from those threats Microsoft offers cyber security
Microsoft EM+S solution provides a response to the huge challenge facing companies that need to safely and efficiently manage an
Network security in On-Premise and Cloud is one of the most important moments for safe and correct working of the
Microsoft offers many security products to protect data, apps and infrastructure quickly with built-in security services in Azure. We will overview some
Fundamental flaws in the encryption system used by popular solid-state drives (SSDs) can be exploited by miscreants to easily decrypt
Windows Defender Credential Guard uses virtualization-based security to isolate secrets so that only privileged system software can access them. Unauthorized
The Windows 10 operating system introduces a new way to build, deploy, and service Windows: Windows as a service. Following
Customers with EA and MSPA agreements can now subscribe users to Windows 10 Enterprise E3 or E5 and activate their
Microsoft 365 is a new offering from Microsoft that combines Windows 10 with Office 365, and Enterprise Mobility and Security (EMS). For Windows 10 deployment, Microsoft