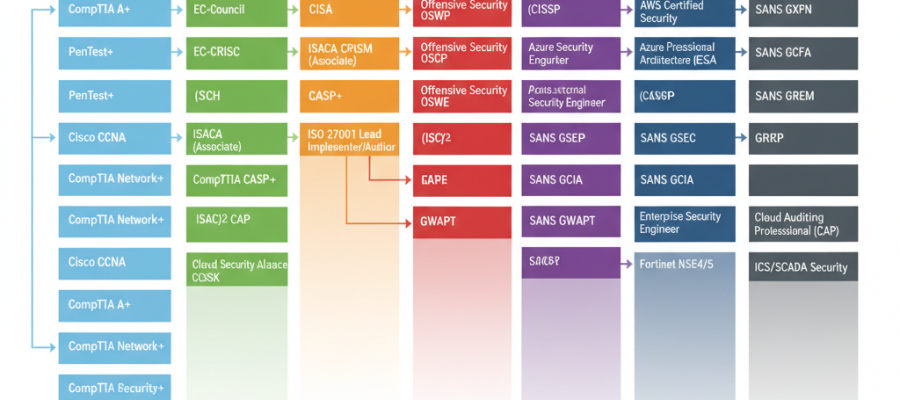
Introduction: Why Cybersecurity Certifications MatterIn an era where digital threats are growing faster than ever, cybersecurity has become one of
The Cyber Security, Compliance & Cloud
Cyber Security | Digital Transformation | Cloud Computing

Introduction: Why Cybersecurity Certifications MatterIn an era where digital threats are growing faster than ever, cybersecurity has become one of
The recent Marks & Spencer (M&S), Co-op Group and Harrods cyber attack (reported in May 2025) involved a sophisticated ransomware attack that disrupted
The Top 25 Most Dangerous Software Errors, often referred to as the CWE (Common Weakness Enumeration) Top 25, is a
The certificates can be public and private Secure Sockets Layer (SSL)/Transport Layer Security (TLS) certificates signed by a certificate authority
As organizations begin to transition services to the cloud, there is a need for ongoing assurances from both cloud customers
Digital forensics, also known as computer and network forensics, has many definitions. It includes identification, collection, examination, and analysis of
FIDO2 is an open authentication standard hosted by the FIDO Alliance that consists of the W3C Web Authentication specification (WebAuthn
Azure Sentinel detects data incidents from connected sources, and then alerts you when action is necessary. You can use Azure
Computing environments move from customer-controlled datacenters to the cloud, the responsibility of security also shifts. Security of the operational environment
It becomes increasingly difficult and challenging to keep corporate confidential and sensitive information’s safe as more employees share files and