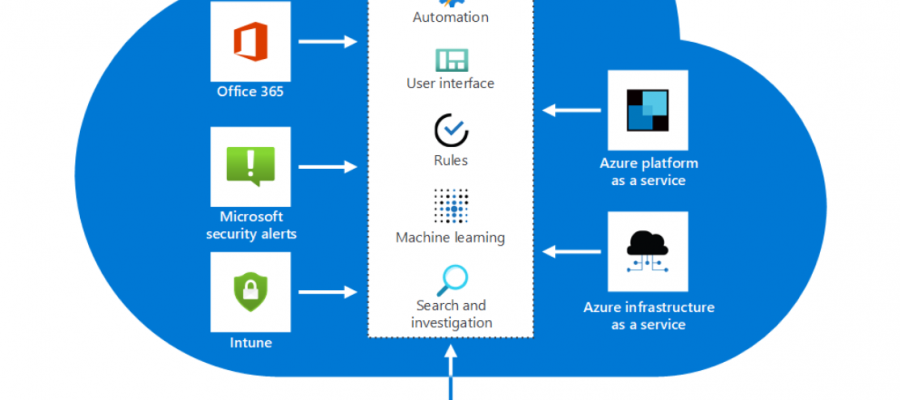
Azure Sentinel detects data incidents from connected sources, and then alerts you when action is necessary. You can use Azure Sentinel overviews, dashboards, and custom queries to gain insights into raw data and potentially malicious events.
After Azure Sentinel retrieves the log data from the services, it performs correlation across data sources. You can manage that data by using the Azure Monitor Log Analytics workspace. Built-in workbooks provide integrated data from your connected data sources. They let you examine the events that those services generate. The built-in workbooks include Azure AD, Azure activity events, and on-premises events. These on-premises events can include data from Windows events from servers or from Microsoft alerts.
Azure Sentinel comes with a number of connectors for Microsoft and other solutions that are available out of the box. There are also built-in connectors to the broader security ecosystem for non-Microsoft solutions. You can also use Common Event Format (CEF), Syslog, or a REST API to connect your data sources with Azure Sentinel. There are connectors for:
Azure Sentinel natively interoperates with these Azure and non-Azure services:
- Azure Activity log
- Azure AD (audit logs and sign-in logs)
- Azure Security Center
- Azure AD Identity Protection
- Azure ATP
- Amazon Web Services CloudTrail
- Cloud App Security
- Domain name servers
- Office 365
- Microsoft Defender ATP
- Azure Web Application Firewall
- Windows Defender Firewall
- Windows security events
User and entity behavior analytics (UEBA) is natively built into Azure Sentinel targeting use-cases such as abuse of privileged identities, compromised entities, data exfiltration, and insider threat detection. Azure Sentinel collects logs and alerts from all of its connected data sources, then analyzes them and builds baseline behavioral profiles of your organization’s entities (users, hosts, IP addresses, applications, and more) across peer groups and time horizons.
Azure Sentinel has built-in roles, If the built-in Azure roles don’t meet the specific needs of your organization, you can create your own custom roles. Just like built-in roles, you can assign custom roles to users, groups, and service principals for management-group, subscription, and resource-group scopes. You can also use Azure RBAC to create and assign roles in your SecOps team. Azure RBAC lets you grant appropriate access to Azure Sentinel.
The following are the three dedicated, built-in Azure Sentinel roles:
- Reader: This role can review data, incidents, workbooks, and other Azure Sentinel resources.
- Responder: This role has all the permissions of the Reader role. Plus, it can manage incidents by assigning or dismissing them.
- Contributor: This role has all the permissions of the Reader and Responder roles. Also, it can create and edit workbooks, analytics rules, and other Azure Sentinel resources. To deploy Azure Sentinel on your tenant, you need Contributor permissions for the subscription where the Azure Sentinel workspace is deployed.
Azure Sentinel bills based on the volume of data that’s ingested for analysis in Azure Sentinel and that’s stored in the Log Analytics workspace. There are two ways to pay for the Azure Sentinel service: Capacity Reservations and pay-as-you-go. Once Azure Sentinel is enabled on your Azure Monitor Log Analytics workspace, every GB of data ingested into the workspace can be retained at no charge for the first 90 days. Retention beyond 90 days will be charged as per the standard Azure Monitor Log Analytics retention prices.