Azure Sentinel is Microsoft’s cloud-native SIEM solution and the first cloud-native SIEM from a major public cloud provider. Azure Sentinel is deployed in an organization’s Azure tenant and accessed via the Microsoft Azure portal, ensuring alignment with preexisting organizational policies.
Azure Sentinel allows organizations to ingest, correlate, and analyze security signals from across the enterprise. Additionally, Azure Sentinel can make use of infrastructure as a service (IaaS) and platform as a service (PaaS) available in Azure to deliver capabilities like workflow automation and long-term log retention that is typically
provided as add-on services from other SIEM providers.
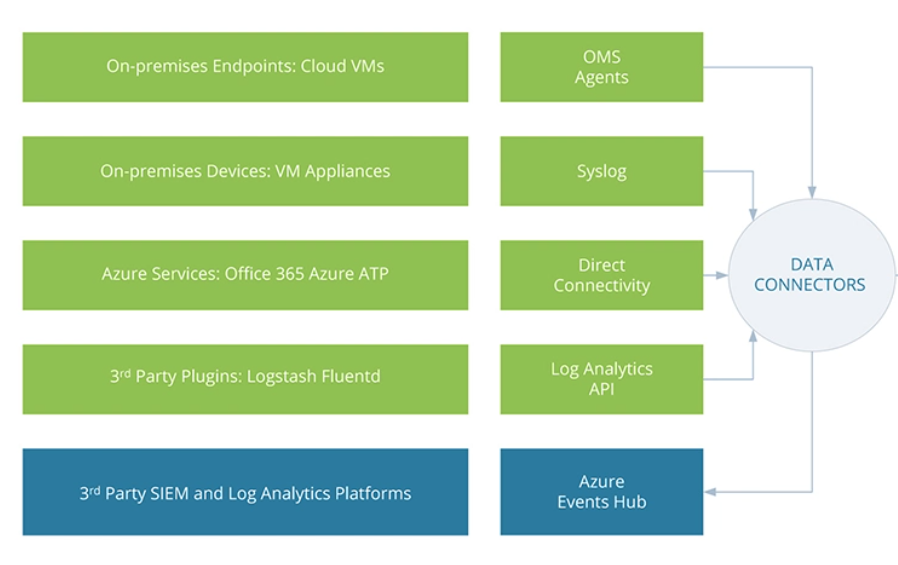
Azure Built-in Connectors
Azure Sentinel includes many connectors that can be deployed in a few clicks via the Azure Sentinel portal and the requisite RBAC permissions. This includes Azure Active Directory, Azure subscription activity, Office 365,
and the whole family of Microsoft Defender products. New data connectors for other products are added on a regular basis. Consider the built-in data connectors over custom ones, where feasible, as they are fully supported by Microsoft and the Azure Sentinel community.
This list is not actively maintained anymore. Refer to the Azure Sentinel connector documentation for more information.
Syslog and CEF
Most network and security systems support either Syslog or CEF (which stands for Common Event Format) over Syslog as means for sending data to a SIEM. This makes Syslog or CEF the most straightforward ways to stream security and networking events to Azure Sentinel.
The advantage of CEF over Syslog is that it ensures the data is normalized, making it more immediately useful for analysis using Sentinel. However, unlike many other SIEM products, Sentinel allows ingesting unparsed Syslog events and performing analytics on them using query time parsing.
The number of systems supporting Syslog or CEF is in the hundreds, making the table below by no means comprehensive. The table links the source device’s vendor documentation for configuring the device to send events in Syslog or CEF.
Direct
Most Microsoft cloud sources and many other clouds and on-prem systems can send to Azure Sentinel natively. For Microsoft Azure sources, this often uses their diagnostics feature.
Agent
The Log Analytics agent can collect different types of events from servers and endpoints listed here. Windows and Linux machines deployed on-premises or in any other cloud environments. Microsoft Internet Information Server (IIS) Web Servers logs can be collected via this agent. Any logs from other applications running on the same machine where MMA agent is running. This is collected via MMA Custom Log settings.
Threat Intelligence (TI)
You can use one of the threat intelligence connectors:
- Platform, which uses the Graph Security API
- TAXII, which uses the TAXII 2.0 protocol
to ingest threat intelligence indicators, which are used by Azure Sentinel’s built-in TI analytics rules, and to build your own rules.
Custom: Logic Apps, Logstash, Azure Functions, Rest API and others
In addition to CEF and Syslog, many solutions are based on Sentinel’s data collector API and create custom log tables in the workspace. Those belong to 3 groups:
- Sources that support Logstash have an output plug-in that can send the events to Azure Sentinel.
- Sources that have native support for the API.
- Sources for which there is a community or Microsoft field-created solution that uses the API, usually using Logic Apps or an Azure function.
- As a low-footprint, relatively inexpensive resource, Azure Function Apps are one of the most stable and performant log ingestion methods. Functions apps provide the full capabilities of .Net, Python, PowerShell, and recently, Node.js and can be used to perform a wide range of log ingestion tasks, including but not limited to log retrieval via REST APIs, pagination, filtering or parsing, and enrichment of data.
Automation and integration
While all the types above focused on getting telemetry into Azure Sentinel, connectors marked as automation/integration enable Azure Sentinel to implement other use cases such as sending information to another system or performing an action on another system. Those might be API-based on integration or Logic App-based integrations.
The main engine behind the Azure Sentinel automation capability is Azure Logic Apps. Azure Sentinel playbooks can perform very advanced tasks with activities branching based on criteria identified in alerts or data retrieved using indicators collected in alerts. The full processing can be performed within the Azure Sentinel environment and is limited only by the automation capabilities provided by the third-party security controls required to provide information or perform additional tasks.
The Grand List
The wide variety of potential data types as log sources means that the consideration paid to each
different data type is important at the outset of an Azure Sentinel project. Azure Sentinel includes
more than 100 connectors, out of the box, with the ability to create custom sources to meet individual
requirements. We have collected a summary table of some of the more common data source types, with
experiential commentary relevant for deployment teams configuring new data ingest sources.
| Vendor | Product | Connector Type | Connecting and using |
| Agari | Phishing Defense and Brand Protection | Built-in (Function, Graph Security API) | Instructions |
| AI Vectra | Detect | Built-in (CEF) | Instructions |
| Akamai | Built-in (CEF) | Instructions | |
| Alcide | kAudit | Built-in (API) | Instructions |
| AlgoSec | ASMS | CEF | Instructions and examples |
| Anomali | Limo | Built-in (TAXII) | Instructions |
| Anomali | ThreatStream | Built-in (TI Platform) | Instructions |
| Anomali | Match | Integration | Overview and instructions |
| Apache | httpd | Built-in (Agent custom logs) | InstructionsAlso, read using rsyslog or logger as a file forwarder for an alternative method. |
| Apache | Kafka | Logstash | See Logstash plug-in. Use to get events sent using Kafka, not for Kafka’s own audit events. |
| Aruba | ClearPass | CEF | Instructions |
| AT&T Cyber | AlienVault OTX | TI (Platform) | Using Logic Apps, See instructions |
| AWS | CloudTrail | Built-in | Sentinel built-in connector |
| AWS | CloudTrail S3 logs | Custom | Using an Azure Function. See here.Using an AWS Lambda Function. See here. |
| AWS | CloudWatch | Logstash | See Logstash Plug-in. |
| AWS | Kinesis | Logstash | See Logstash Plug-in. |
| AWS | Object Level S3 Logging | Logstash | See here. |
| AWS | Security Hub | Custom | Azure Function. See here. |
| Barracuda | WAF | Built-in (API) | Instructions |
| Barracuda | CloudGen Firewall | API | Sentinel built-in connector |
| BETTER Mobile | Threat Defense | Built-in (API) | Instructions |
| Beyond Security | beSECURE | Built-in (API) | Instructions |
| Carbon Black | Cloud Endpoint Standard (Cb Defense) | Built-in (Function)Syslog | Sentinel built-in connector Instructions |
| Carbon Black | (Cb Response) | Syslog | Instructions |
| Checkpoint | CEF | Sentinel Built-in connector | |
| Cisco | ACS | Syslog | Instructions |
| Cisco | ASA | Cisco (CEF) | Sentinel built-in connectorNotes:- Cisco ASA support uses Sentinel’s CEF pipeline. However, Cisco’s logging is not in CEF format.- Make sure you disable logging timestamp using “no logging timestamp”. See here for more details. |
| Cisco | Cloud Security Gateway (CWS) | CEF | Use the Cisco Advanced Web Security Reporting. |
| Cisco | FTD | Cisco (CEF) | FTP Platform logs are compatible with ASA logs and can use the same connector (see here). |
| Cisco | IOS | Syslog | Instructions |
| Cisco | ISE (NAC) | Syslog | Instructions |
| Cisco | Web Security Appliance (WSA) | CEF | Use the Cisco Advanced Web Security Reporting. |
| Cisco | Meraki | Syslog | InstructionsEvent Types and Log Samples |
| Cisco | eStreamer | CEF | Using enCore |
| Cisco | Firepower Threat Defense | CEFSyslog | Using eStreamer enCoreInstructions, Event reference |
| Cisco | FireSight | CEF | Using eStreamer enCore |
| Cisco | IronPort Web Security Appliance | Syslog | Instructions |
| Cisco | Nexus | Syslog | Instructions |
| Cisco | Umbrella | Built-in (Function) | InstructionsAlso, see this blog postfor a custom solution |
| Cisco | Unified Computing System (UCS) | Built-in (Syslog) | Instructions |
| Cisco | Viptela SD-WAN | Syslog | Instructions |
| Citrix | Analytics | Built-in (Direct) | Instructions |
| Citrix | NetScaler | Syslog | InstructionsMessage format |
| Citrix | NetScaler App FW | Built-in (CEF) | Instructions |
| Clearswift | Web Security Gateway | Syslog | Instructions |
| Cloudflare | Use Cloudflare Logpush to send to storage and a custom connector to read events from storage (for example, reading AWS S3 buckets). | ||
| Cribl | LogStream | Direct | Instructions |
| CrowdStrike | Falcon | CEF | Instructions. Use a SIEM connector installed on-premises. |
| CyberArk | Endpoint Privilege Manager (EPM) | SyslogLogstash | Instructions (for both) |
| CyberArk | Privileged Access Security (PTA) | CEF | InstructionsMessage format |
| Darktrace | Immune | CEF | See announcement. Contact vendor for instructions. |
| Digital Guardian | CEF | 3rd party instructions | |
| DocuSign | Monitor | Custom | See this blog post |
| Duo Security | CEF | Using Duo LogSync | |
| Extrahop | Reveal | Built-in (CEF) | Instructions |
| F5 | ASM (WAF) | Built-in (CEF) | Instructions |
| F5 | BigIP (System, LTM, AFM, ASM, APM, AVR) | Built-in (Direct) | Instructions |
| Fastly | WAF | Custom | See this blog post (Logic Apps or Azure Function) |
| Forcepoint | Web Security (WebSense) | CEF | InstructionsDetailed reference |
| Forcepoint | CASB | CEF | Sentinel built-in connector |
| Forcepoint | DLP | Direct | Sentinel built-in connector |
| Forcepoint | NGFW | CEF | Sentinel built-in connector |
| Forescout | CounterAct | CEF | Instructions |
| Fortinet | CEF | Sentinel built-in connectorLog message referenceCEF mapping and examples | |
| Fortinet | FortiSIEM | CEF | Instructions |
| Fortinet | FortiSOAR | Integration | Instructions |
| GitHub | Custom | See connector, rules, and hunting queries here | |
| GCP | Cloud Storage | Logstash | See Plug-in. Use to get events stored in GCP Cloud Storage, not for Cloud Storage own audit events. |
| GCP | Pub/Sub | Logstash | See Plug-in. Use to get events sent using Pub/Sub, not for Pub/Sub own audit events. |
| GCP | Stacdriver | Logstash Custom | Through GCP Cloud Storage or GCP Pub/Sub as described above. Using GCP Cloud Function. See here. |
| Group-IB | Custom (TI Platform) | Using Logic Apps. See instructions | |
| GuardiCore | Centra | CEF | Contact vendor for instructions |
| HP | Printers | Syslog | Instructions |
| IBM | iSeries | CEF | See here. |
| IBM | QRadar events | Syslog | Forward raw events or correlation events in raw, parsed, or JSON format. See instructions. |
| IBM | QRadar offenses | Custom (Function) | Blog post |
| IBM | X-Force | TI (TAXII) | Instructions |
| IBM | zSecure | CEF | See What’s new for zSecure V2.3.0Note that it supports alerts only. |
| Illusive | Attack Management System | Syslog | Sentinel built-in connector |
| Imperva | SecureSphere | CEF | Instructions |
| Infoblox | NIOS | Built-in (Syslog) | Instructions |
| InSights | TI (TAXII) | TAXII Instructions and related workbook | |
| Jamf | Pro | Syslog | Instructions |
| Juniper | ATP | CEF | Instructions |
| Juniper | JunOS based devices | Built-in (Syslog) | Instructions |
| Kaspersky | Security Center | CEF | Instructions |
| ManageEngine | AD Audit Plus | CEF | Instructions (use ArcSight instructions) |
| ManageEngine | Exchange Reporter Plus | Syslog | Instructions |
| McAfee | ePO | Syslog | Instructions (Note: TLS only (requires rsyslog TLS configuration) |
| McAfee | MVISION EDR | Syslog | Instructions |
| McAfee | Web Gateway | CEF | Instructions |
| Microfocus | Fortify AppDefender | CEF | Instructions (require authentication; contact vendor for further details). |
| Microsoft | Active Directory | Agent | Most AD events are logged as part of security events. Also, See in this list:LDAP auditingSMBv1 auditing |
| Microsoft | Advanced Threat Protection (ATA) | CEF | InstructionsLog reference |
| Microsoft | Azure Active Directory (AAD) | Built-in (Diagnostics) | InstructionsDetections: Sign-in Logs, Audit LogsBuilt-in workbooks:Azure AD Audit Logs,Azure AD Audit, Activity and Sign-in LogsAzure AD Sign-in logsWebinars: “A day in a SOC analyst life” (YouTube, MP4, Presentation)”Tackling Identity” (YouTube, MP4, Presentation) |
| Microsoft | Azure Active Directory Domain Services | Diagnostics | InstructionsUse Workbooks to analyze |
| Microsoft | Azure Active Directory Identity Protection | InstructionsAlert information | |
| Microsoft | AzureAzure ActivityAzure SubscriptionsAzure Management Groups | Direct | Built-in connector,Connect through the subscription diagnostic settings to ensure lower latency and broader collection.For Management groups, Use the API to turn on diagnostics settingsAzure Activity schemaDetections |
| Microsoft | Application Insights | Direct | Send to a sentinel workspaceOr use queries across workspaces |
| Microsoft | App Services & Web Application monitoring | Direct | Instructions and reference architecture |
| Microsoft | Azure B2B | Direct | Included as part of AAD events |
| Microsoft | Azure B2C | Direct | collect B2C logs from your B2C tenant to your primary tenant AAD logs as described here |
| Microsoft | Azure Cosmos DB | Direct | Instructions |
| Microsoft | Azure Data Lake Gen 1 | Direct | InstructionsQuery examples |
| Microsoft | Azure Data Factory | Direct | Instructions |
| Microsoft | Azure Databricks | Direct | Instructions |
| Microsoft | Azure DDOS | Built-in (diagnostics) | Built-in connectorDiagnostics instructionsEnable collection using PowerShellWebinar: Detecting and Responding to Threats using Azure Network Security tools and Azure Sentinel |
| Microsoft | Azure Defender and Azure Security Center (ASC) | Direct | Built-in connector for getting ASC alerts Alert list and alert schema.Use Azure Defender’s continuous export feature to get recommendations, findings, secure score, and compliance data to Sentinel. |
| Microsoft | Azure Defender for IoT | Built-in (Direct) | InstructionsAlerts Overview |
| Microsoft | Azure DevOps | Direct | Instructions |
| Microsoft | Azure Event Hub (subscription) | Logstash | See Logstash Plug-in. Use to get events sent using an Event Hub, not for Event Hub own audit events. |
| Microsoft | Azure Files | Direct (Diagnostics) | InstructionsSchema information |
| Microsoft | Azure Firewall | Built-in (diagnostics) | Built-in connectorWorkbookEnable collection using PowerShell or diagnosticsWebinar: Detecting and Responding to Threats using Azure Network Security tools and Azure Sentinel |
| Microsoft | Azure Front Door | Direct | Instructions |
| Microsoft | Azure Key Vault (AKV) | Built-in (Diagnostics) | Connect:Instructions (Built-in, Using policy)Enable AKV diagnostics using the portalEnable AKV diagnostics using PowerShellUse:Log schemaDetection rulesWorkbook |
| Microsoft | Azure Information Protection (Classic and Unified Labeling) | Built-in (Direct) | Instructions |
| Microsoft | Azure Kubernetes Service (AKS) | Direct | Blog post: Monitoring Azure Kubernetes Service (AKS) with Azure SentinelDocumentation: Enable Azure Monitor for containers |
| Microsoft | Azure Log Analytics | Direct | Collect query auditing and other metrics: Instructions |
| Microsoft | Azure Logic Apps | Direct | Instructions |
| Microsoft | Azure Network Security Groups (NSG) | Direct | Flow logsRule activationWebinar: Detecting and Responding to Threats using Azure Network Security tools and Azure Sentinel |
| Microsoft | Azure SQL | Built-in (diagnostics) | Built-in connectorDiagnostics settings instructions |
| Microsoft | Azure SQL Managed Instance | Direct | Instructions |
| Microsoft | Azure Site Recovery | Direct | Instructions |
| Microsoft | Azure Storage | Direct | InstructionsBlog: Blob and File Storage Investigations |
| Microsoft | Azure Storage Content | Custom (Azure Function) | Ingest the content of Azure Storage Blobs. See GitHub. |
| Microsoft | Azure Synapse | Direct | Instructions |
| Microsoft | Azure Web Application Firewall (WAF) | Built-in (Diagnostics) | Blog postBuilt-in connectorWebinar: Detecting and Responding to Threats using Azure Network Security tools and Azure Sentinel |
| Microsoft | BitLocker / MBAM | Agent | Using Windows Event collection. Blog post |
| Microsoft | Cloud App Security (Alerts, Discovery logs) | Built-in (Direct) | InstructionsAlerts Information |
| Microsoft | Cloud App Security (Activity Log) | CEF | Instructions |
| Microsoft | Defender for Office | Built-inCustom | For AIRs alerts: instructionsFor other alerts: Use Either a Logic App or an Azure function custom connector. For the Azure Function connector, query for RecordType_d == “28”, “41” or “47” . |
| Microsoft | Defender for Identity (Azure ATP) Alerts | Built-in | Instructions (Direct)Instructions (Microsoft 365 Defender) Alerts overview |
| Microsoft | Defender for Identity (Azure ATP) Events | CEF | InstructionsLog reference |
| Microsoft | Desktop Analytics | Direct | Connect |
| Microsoft | DNS | Agent | Sentinel built-in connector |
| Microsoft | Dynamics 365 | Built-in | Sentinel built-in connector |
| Microsoft | Dynamics (not 365) | Agent | Using IIS logsUsing Dynamics Trace Files |
| Microsoft | IIS | Agent | Instructions |
| Microsoft | Intune | Direct | ConnectUse cases |
| Microsoft | LDAP (Windows Server) | Agent | Configure AD diagnostics logging and set “16 LDAP Interface Events” to 2 or above. |
| Microsoft | Office 365 (Exchange, SharePoint, OneDrive, DLP Alerts) | Built-in | Sentinel built-in connectorFor details about DLP alerts, read here. |
| Microsoft | Office 365 (Microsoft Defender for Office; formerly Office ATP, PowerBI, Yammer, Sway, Forms, eDiscovery, and others) | Custom (Azure Function, Logic Apps) | Use Either a Logic App or an Azure function custom connector |
| Microsoft | Office 365 e-mail trace logs | Custom (Logic Apps) | See Blog Post. |
| Microsoft | PowerBI Embedded | Direct (Diagnostics) | Instructions |
| Microsoft | SMBv1 (Windows Server) | Agent | See Enable Auditing on SMB Servers, and the CmdLet reference |
| Microsoft | Teams (Call Logs) | Custom | Using Logic Apps |
| Microsoft | Teams (Management Activity) | Built-in | Use the built-in Office 365 connectorUse the Hunting use cases or Graph Visualization of External MS Teams Collaborations.Understand the Teams event schemaUse the custom Logic App or Azure function connectors for special use cases.Expanding Microsoft Teams Log Data in Azure Sentinel:Extracting Teams file-sharing informationMapping Teams logs to Teams call recordsMerging Teams logs with sign-in activity to detect anomalous actions |
| Microsoft | Teams Shifts | Custom | Use Either a Logic App or an Azure function custom connector. For the Azure Function connector, query for RecordType_d == “73” |
| Microsoft | SCCM | Agent | Instructions |
| Microsoft | SQL Server | Agent | Instructions, parser, rules, and hunting queriesYou can also audit at the engine level. |
| Microsoft | Sysmon | Agent | Using Windows Event collection. Blog post |
| Microsoft | Windows (Security Events) | Agent | Sentinel built-in connectorEnriching Windows Security Events with Parameterized Function |
| Microsoft | Windows (Other Events, Sysmon) | Agent | Instructions |
| Microsoft | Windows network connections | Agent | VM InsightsWire Data |
| Microsoft | Windows Firewall | Agent | Sentinel built-in connector |
| Microsoft | Windows Virtual Desktop | Direct | Connect using the portal and samples queriesConnect using PowerShell and Sample queriesBlog post covering connecting and using: Monitoring Windows Virtual Desktop environmentsCommon error codes |
| Mimecast | Agent | Announcement. For technical instructions, contact the vendor. | |
| Minerva Labs | CEF | Please ask the vendor for instructions. | |
| MISP | TI (Platform) | Sentinel built-in connector | |
| NetApp | ONTAP | Syslog | InstructionsNote that those are management activity audit logs and not file usage activity logs. |
| Netflow | Logstash | Use the Netflow codec plug-in | |
| Nexthink | CEF | Instructions | |
| Nozomi | Guardian | CEF | Contact vendor for details |
| NXlog | Direct | Instructions | |
| Okta | SSO | Built-in (Function) | Instructions |
| One Identity | Safeguard | Built-in (CEF) | Instructions |
| Oracle | Cloud (OCI) | Custom (Azure Function) | Available Here |
| Oracle | DB | Syslog | Instructions |
| Orca | Built-in (API) | Instructions | |
| OSSEC | CEF | Instructions | |
| Pager Duty | Automation (Playbook) | Blog post | |
| Palo Alto | Cloudgenix | Syslog | Instructions |
| Palo Alto | Minemeld | TI (Platform) | Sentinel built-in connector |
| Palo Alto | PanOS | CEF | Sentinel built-in connector |
| Palo Alto | Panorama | CEF | Instructions |
| Palo Alto | Prisma | SyslogCustom | Instructions, FieldsLogic Apps using a Webhook and clarification |
| Palo Alto | Traps through Cortex | Syslog | InstructionsNotes:- Require rsyslog configuration to support RFC5424- TLS only (requires rsyslog TLS configuration)- The certificate has to be signed by a public CA |
| Palo Alto | XDR | CEF | Instructions |
| Palo Alto | XSOAR | Integration | Forward Azure Sentinel incidents to Palo Alto XSOAR |
| Perimeter 81 | Built-in (API) | Instructions | |
| Ping Identity | Federate | CEF | Instructions |
| Ping Identity | Provisioner | CEF | Instructions |
| Postgress | DB | Syslog, Windows Event log | Instructions |
| Proofpoint | On Demand | Built-in (API) | Instructions |
| Proofpoint | TAP | Built-in (Function) | Instructions |
| Pulse | Connect | Built-in (Syslog) | Instructions |
| Qualys | VM | Built-in (Function) | Instructions |
| Radware | Cloud WAF | Logstash | Instructions |
| RedHat | OpenShift | Syslog API | Instructions for Syslog Fluentd Log Analytics plugin for API |
| RedHat | Azure OpenShift | Syslog Custom | Instructions for Syslog Fluentd Log Analytics plugin for API |
| RiskIQ | Action (Logic Apps) | Azure Logic-Apps built-in connector | |
| Salesforce | Service Cloud | Built-in (Function) | Instructions |
| SAP | Hana | Syslog | Instructions (requires an SAP account) |
| SentinelOne | CEF | Please consult the vendor for instructions | |
| SNMP | Syslog | Instructions | |
| Snort | Agent | Instructions | |
| SonicWall | CEF | InstructionsMake sure you: – Select local use 4 as the facility.- Select ArcSight as the Syslog format. | |
| Sophos | Central | CEF | Instructions. Note that the script provided by Sophos has to be scheduled using a cron job, which is not documented on the reference page. |
| Sophos | XF Firewall | Built-in (Syslog) | Instructions |
| Squadra | secRMM | Built-in (API) | Instructions |
| Squid Proxy | Built-in (Agent)Syslog | Instructions Configure access logs with either the TCP or UDP modules. Sentinel’s built-in queries use the default log format. | |
| Symantec | DLP | SyslogCEF | Instructions. Note that only UDP is supportedInstructions. Uses response automation. |
| Symantec | ICDX | Built-in (API) | Instructions |
| Symantec | Proxy SG (Bluecoat) | Built-in (Syslog) | Instructions |
| Symantec | Endpoint Protection Manager | Syslog | Instructions |
| Symantec | Cloud Workload Protection | API | Instructions |
| Symantec | VIP | Built-in (Syslog) | Instructions |
| TheHive | Integration | Send new incidents to TheHive | |
| Thinkst | Canary | Syslog | Instructions |
| ThreatConnect | TI (Platform) | Sentinel built-in connector | |
| ThreatQuotient | TI (Platform) | Sentinel built-in connector | |
| Thycotic | Secret Server | CEF | Instructions |
| TitanHQ | WebTitan Cloud | Syslog | Instructions |
| Trend Micro | CEF | Using Control ManagerUsing LogForwarder | |
| Trend Micro | Apax Central (Cloud and On-prem) | CEF | Instructions |
| Trend Micro | Deep Security | CEF | Sentinel built-in connector |
| Tufin | SecureTrack | Syslog | Instructions |
| Varonis | DatAlert | CEF | Instructions |
| WatchGuard | CEF | Instructions | |
| Zimperium | Mobile Threat Defense | Built-in (API) | Instructions |
| zScaler | Internet Access (ZIA) | Built-in (CEF) | Instructions |
| zScaler | Private Access (ZPA) | Logstash | Use LSS. Since LSS sends raw TCP but not Syslog, you will have to use Logstash and not Azure Sentinel’s native connector. |
| Zoom | Custom | Using Azure Function. |