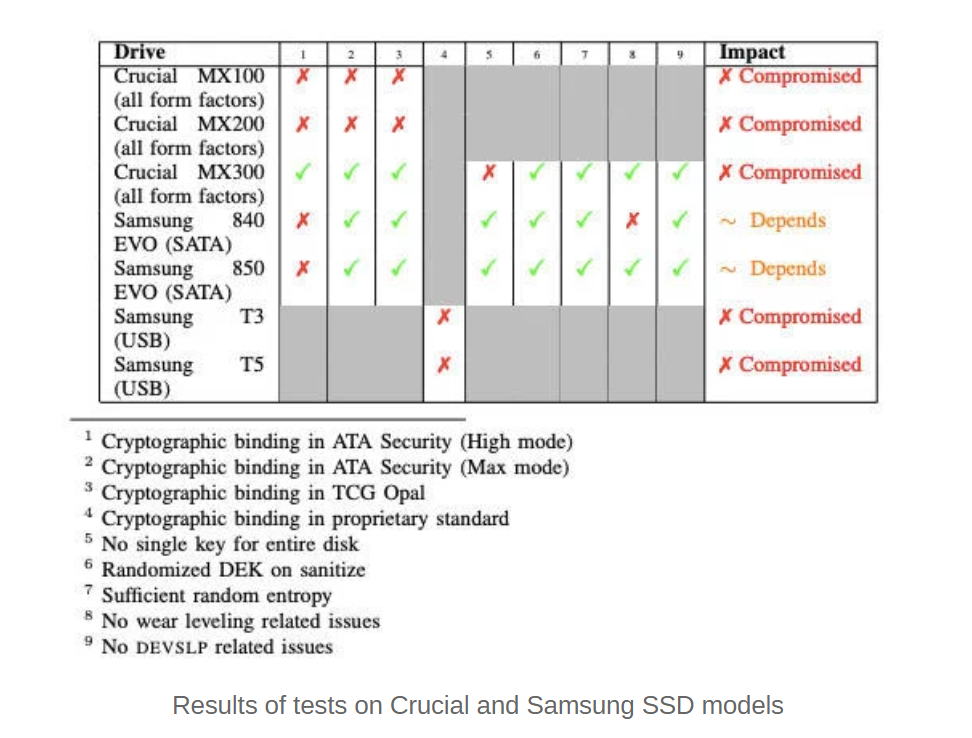
Fundamental flaws in the encryption system used by popular solid-state drives (SSDs) can be exploited by miscreants to easily decrypt data.
“The analysis uncovers a pattern of critical issues across vendors,” according to the researchers. “For multiple models, it is possible to bypass the encryption entirely, allowing for a complete recovery of the data without any knowledge of passwords or keys.”
A paper [PDF] drawn up by researchers Carlo Meijer and Bernard van Gastel at Radboud University in the Netherlands, and made public today, describes these critical weaknesses. The bottom line is: the drives require a password to encrypt and decrypt their contents, however this password can be bypassed, allowing crooks and snoops to access ciphered data.
Researchers could retrieve the keys by modifying the drive’s firmware, or by exploiting a code injection vulnerability that would also allow an attacker to modify the password routine – both require physical access to the drive.
Unfortunately, the pair also note that some popular data encryption systems, including the BitLocker tool Microsoft uses in Windows 10, do not use software encryption for SSDs and rely on the drive’s vulnerable hardware encryption.
Microsoft advisory is to switch to software encryption to mitigate risk
Check your Drive Encryption Status
To check the type of drive encryption being used (hardware or software):
- Run ‘manage-bde.exe -status’ from an elevated command prompt.
- If none of the drives listed report “Hardware Encryption” for the Encryption Method field, then this device is using software encryption and is not affected by vulnerabilities associated with self-encrypting drive encryption.
Switch to Software Encryptions
Microsoft Advisory: For drives that are encrypted using a vulnerable form of hardware encryption, you can mitigate the vulnerability by switching to software encryption using with a Group Policy.
Note: After a drive has been encrypted using hardware encryption, switching to software encryption on that drive will require that the drive be unencrypted first and then re-encrypted using software encryption. If you are using BitLocker Drive Encryption, changing the Group Policy value to enforce software encryption alone is not sufficient to re-encrypt existing data.
To mitigate vulnerabilities associated with self-encrypting drives on Windows systems:
- Configure and deploy a Group Policy to enable forced software encryption.
- Fully turn off BitLocker to decrypt the drive.
- Enable BitLocker again.
Use Intune to Force settings
- Get the GPO key HKLM:\SOFTWARE\Policies\Microsoft\FVE
FDVHardwareEncryption = 0 (dword) - Use Intune PowerShell to apply the setting
BitLocker Policy Settings for software-based encryption
This policy setting allows you to manage BitLocker’s use of hardware-based encryption on fixed data drives and specify which encryption algorithms it can use with hardware-based encryption.
| Registry Hive | HKEY_LOCAL_MACHINE |
| Registry Path | SOFTWARE\Policies\Microsoft\FVE |
| Value Name | FDVHardwareEncryption |
| Value Type | REG_DWORD |
| Enabled Value | 1 |
| Disabled Value | 0 |
Use BitLocker software-based encryption when hardware encryption is not available, You can allow failover
Restrict encryption algorithms and cipher suites allowed for hardware-based encryption
Restrict crypto algorithms or cipher suites to the following:
Reference:
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/ADV180028
https://forums.theregister.co.uk/forum/1/2018/11/05/busted_ssd_encryption/