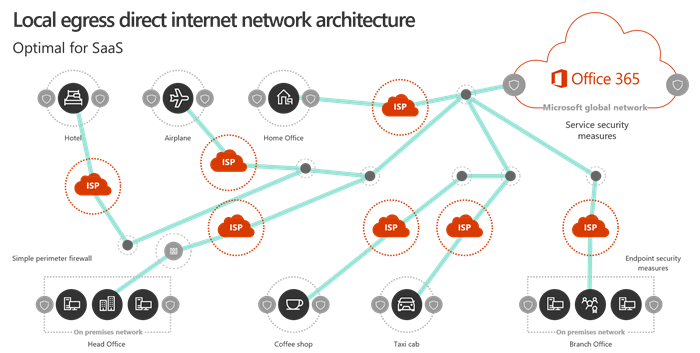
Office 365 connectivity can be optimized by implementing a combination of approaches like network route optimization, firewall rules, browser proxy
The Cyber Security, Compliance & Cloud
Cyber Security | Digital Transformation | Cloud Computing

Office 365 connectivity can be optimized by implementing a combination of approaches like network route optimization, firewall rules, browser proxy
Network security in On-Premise and Cloud is one of the most important moments for safe and correct working of the
Amazon has been a fore runner in the cloud computing arena and pioneered many industry revolutionizing services like EC2, VPC
What is OSI model?The OSI model (Open System Interconnection) model defines a computer networking framework to implement protocols in seven
Active Directory has five special roles which are vital for the smooth running of AD as a multimaster system. Some
The purpose of system hardening is to eliminate as many security risks as possible. This is typically done by removing
Domains are managed by using a worldwide system of domain registrars and databases. The Domain Name System DNS are the
The OSI model consolidates network communications into seven simplified layers. So what are the seven layers? Below, I list them
I hope we all know how to login to Switch by telnet or putty etc. After successful logon Type Config
To access DOS command press Windows Key + R on your keyboard. The other way to access the DOS Command