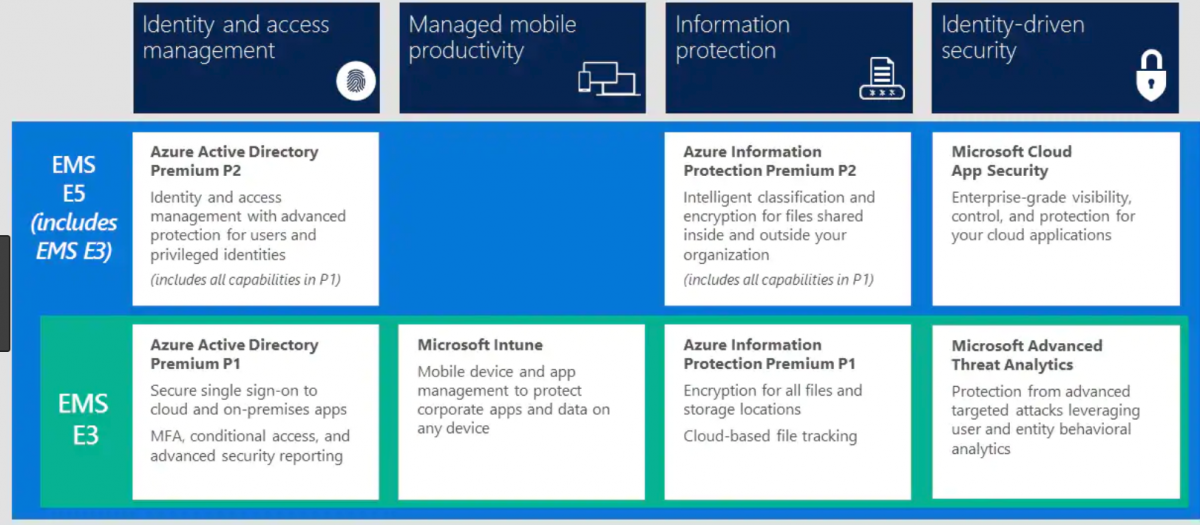
Microsoft EM+S solution provides a response to the huge challenge facing companies that need to safely and efficiently manage an increasingly mobile workforce, the Bring Your Own Device (BYOD) trend and Identity Management. Microsoft EM+S is a cloud-based offering (SaaS), licensed on a per user base.
Components of Enterprise Mobility + Security (EM+S)
| Component | Summary |
| Azure Active Directory Premium | Identity and Access Management Solution, Control identity + access in the cloud and provide solution |
| Microsoft Intune | Mobile Application and Mobile Device Management Solution |
| Azure Information Protection | Data and Information Protection Solution |
| Microsoft Advanced Threat Analytics / Advance Threat Protection | Cybersecurity and Risk Management Solution |
Cloud Apps Security | Keep you in control, through improved visibility into activity. |
Azure Active Directory Premium
Staying in control of your identity security has never been more important and cloud identity and access management is vital. With industry-leading solutions such as conditional access, identity protection and password protection, Azure AD holds the key.
Your employees can sign into almost any service regardless of model, location, or user identity. i.e
- File Servers
- Application Servers
- Database Servers
- Cloud-based Applications
- Third Party & Bespoke Applications
- Mobile and On-premise Devices
The big deal about Azure Active Directory Premium is this: it enables single-sign-on to cloud software and on-premise software. With one password you can access almost everything, including thousands of SaaS cloud apps. Other useful features include:
Azure Active Directory Offers:
- Self-service password reset to reduce helpdesk calls
- Multi-factor authentication options for greater security
- Group-based provisioning and single sign-on for thousands of SaaS apps
- Machine learning-driven security reports for visibility and threat management
- Robust sync capabilities across cloud and on-premises directories
- Conditional access: block people from logging in based on various factors
- Reporting on logins and the meta-data associated with access requests
- Identity and Access Management with advanced protection for Users and Privileged users
Microsoft Intune
Microsoft Intune is a cloud-based enterprise mobility management (SaaS) product that helps organizations to manage the mobile devices, have the productive workforce, consistent and secure access to corporate resources and data from any location on any device.
Microsoft Intune allows you to link an unlimited number of mobile devices to an employees’ Active Directory profile. Microsoft Intune is your secure link between an employee’s mobile device (iOS, Android, Windows) and corporate data.
Microsoft Intune offers:
- Mobile application management across devices
- Broad device support for iOS, Android, Windows and Windows Phone devices
- Selective wipe of apps and data for greater security
- Use of System Center Configuration Manager and Endpoint Protection
- Secure Access to Emails, On-premise and cloud applications
- Secure access to company data using Microsoft Apps
Azure Information Protection (AIP)
Azure Information Protection (sometimes referred to as AIP) is a cloud-based solution that provides document-level security. The organisation can
add persistent classification, labelling and protection of the sensitive information they share both internally and externally with Microsoft Azure Information.
Azure Rights Management offers:
- Classification and labelling: Configure policies to classify, label and protect data based on its sensitivity. Classification with Azure Information Protection is fully automatic, driven by users or based on a recommendation.
- Intelligent classification and encryption for files and emails shared inside and outside your organization with P2 Licence
- Encryption and rights management: Encrypt your sensitive data and define usage rights when needed.
- One-click process: Apply protection easily without interrupting your employee’s normal course of work. Data classification and protection controls are integrated into Microsoft Office and common applications to secure the data you’re working on with one click
- Tracking and reporting: See what’s happening with your shared data to gain more control over it. Track activities on shared data and revoke access if necessary.
- Deployment and management flexibility: Help protect your data whether it’s stored in the cloud or in on-premises infrastructures. You have the flexibility to choose how your encryption keys are managed, including Bring Your Own Key (BYOK) options.
Microsoft Advanced Threat Analytics (ATA/ATP)
Advanced Threat Analytics ATA is an on-premises platform that helps protect your enterprise from multiple types of advanced targeted cyber attacks and insider threats by using information from multiple data-sources in your network to learn the of users and other entities in the organization and build a behavioural profile about them.
ATP is available with E5, In contrast, Azure ATP exists as a hybrid solution rather than solely on-premise. Azure ATP parses network traffic via on-premise ATP sensors, which function very similarly to ATA gateways, but all parsed data is sent to the Azure cloud for analysis and reporting. Instead of a local ATA console, all information is presented in the cloud by the Azure ATP workspace portal.
ATA leverages a proprietary network parsing engine to capture and parse network traffic of multiple protocols (such as Kerberos, DNS, RPC, NTLM This information is collected by ATA via:
- Port mirroring from Domain Controllers and DNS servers to the ATA Gateway and/or
- Deploying an ATA Lightweight Gateway (LGW) directly on Domain Controllers
Advanced Threat Analytics Features:
- Behavioural analytics for advanced threat detection
- Detection for known malicious attacks and security issues & surfaces the information in the ATA Console.
- Simple, actionable feed for the suspicious activity alerts and the recommendations including a clear view of Who, What, When and How.
- Integration with your existing Security Information and Event Management (SIEM) systems
- Alert for known risks
What does ATA do?
Microsoft Cloud App Security
It’s a comprehensive solution that can help as you move to take full advantage of the cloud applications, but keep you in control, through improved visibility into activity. Can provide you with the same level of on the premise security to your cloud applications. This feature is only with E5.
Cloud Apps Security Features
- Cloud Discovery: Discover all cloud use in your organization, including Shadow IT reporting and control and risk assessment,
sanction or unsanction apps in your organization by using the Cloud app catalog. - Data Protection: Monitor and control your data in the cloud by gaining visibility, enforcing DLP policies, alerting and investigation.
- Threat Protection: Detect anomalous use and security incidents. Use analytics and advanced investigation tools to mitigate risk and set policies and alerts to achieve maximum control over network cloud traffic.
- Conditional Access App Control protection Microsoft Cloud App Security Conditional Access App Control utilizes reverse proxy architecture to give you the tools you need to have real-time visibility and control over access to and activities performed within your cloud environment.
- Policy ControlsYou can use policies to define your users’ in the cloud. Use policies to detect risky , violations, or suspicious data points and activities in your cloud environment. If needed, you can use policies to integrate remediation processes to achieve complete risk mitigation.