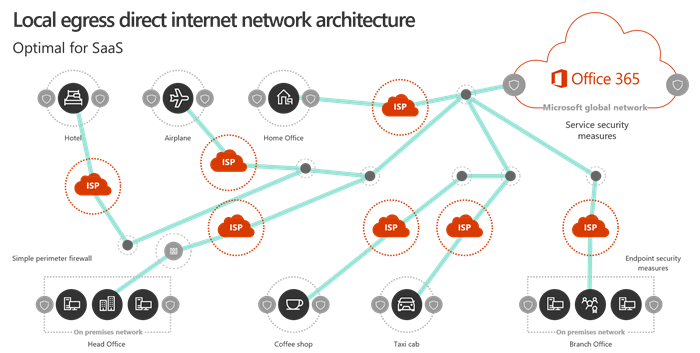
Office 365 connectivity can be optimized by implementing a combination of approaches like network route optimization, firewall rules, browser proxy
The Cyber Security, Compliance & Cloud
Cyber Security | Digital Transformation | Cloud Computing

Office 365 connectivity can be optimized by implementing a combination of approaches like network route optimization, firewall rules, browser proxy
Azure AD identity and access management enable deep security, productivity, and management across devices, data, apps, and infrastructure. It’s an integral
Microsoft EM+S solution provides a response to the huge challenge facing companies that need to safely and efficiently manage an
The Windows 10 operating system introduces a new way to build, deploy, and service Windows: Windows as a service. Following
Customers with EA and MSPA agreements can now subscribe users to Windows 10 Enterprise E3 or E5 and activate their
Microsoft 365 is a new offering from Microsoft that combines Windows 10 with Office 365, and Enterprise Mobility and Security (EMS).For Windows 10 deployment, Microsoft 365
Azure ATP monitors your domain controllers by capturing and parsing network traffic and leveraging Windows events directly from your domain
Azure AD Connect sync is the successor of DirSync, Azure AD Sync, and Forefront Identity Manager with the Azure Active
Azure Active Directory is not designed to be the cloud version of Active Directory. It is not a domain controller
Microsoft System Center Configuration Manager 2012 (SCCM 2012) is a Windows product that enables administrators to manage the deployment and