Azure Active Directory (AAD)
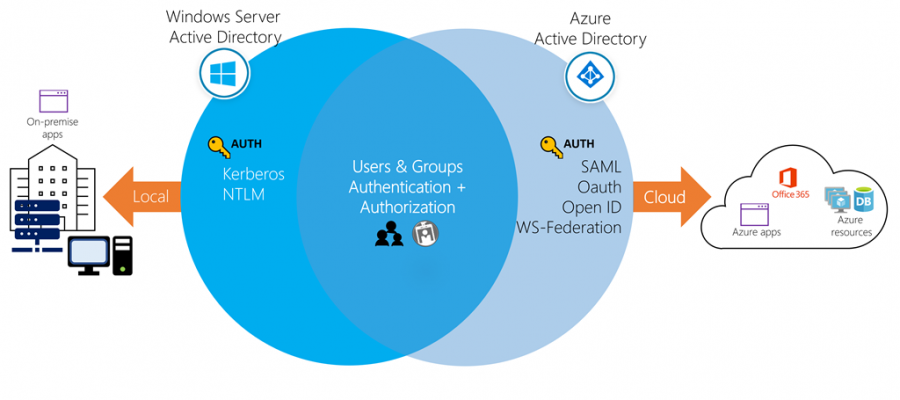
Azure Active Directory (Azure AD) is Microsoft’s cloud-based identity and access management service, which helps your employees sign in and access resources. Azure AD is the backbone of the Office 365 system, and it can sync with on-premise Active Directory and provide authentication to other cloud-based systems, Internal resources, such as apps, intranet via OAuth.
Windows Active Directory
Windows Active Directory lives on-premise in servers called Domain Controllers (DC). Each DC contains a catalogue of users and computers that are authorized to access resources on the network. Users authenticate to DCs via Kerberos or NTLM authentication.
Azure AD and Windows AD are both created by Microsoft, and they are both IAM systems, but that’s pretty much where the comparisons stop. They are fundamentally different systems that exist in an interconnected enterprise environment.
| Azure Active Directory | Windows Active Directory | |
| Communication | REST | LDAP |
| Authentication | Cloud-based protocols | Kerberos and NTLM |
| Network Organisation | Flat Structure of users into groups | OU’s, Domains and forests |
| Devices | Mobile Device Management | No MDM |
| Entitlement Management | Admins organised users into groups | Admins or data owners assign users to groups |
| Desktops | Windows desktops can join Endpoint management | Desktops are governed by GPOs |
| Servers | Uses Domain services to manage servers | Managed by GPOs or On-premise server management system |
Directories, Subscriptions and Users
It’s Important to understand that Azure offers several cloud-based services. All of those services can use Azure AD to identify users and control access.
When a company or organization signs up to use one of these offerings, they are assigned a default directory, which is an instance of Azure AD. This directory holds the users and groups that will have access to each of the services the company has signed up for. This default directory is sometimes referred to as a tenant. A tenant represents the organization and the default directory assigned to it.
An organization (tenant) always has one default Azure AD directory it’s associated with, however, owners can create additional directories to support development or testing purposes, or because they want to have separate directories to synchronize with their local Windows Server AD forests.
Subscriptions in Azure are both a billing entity and a security boundary. Resources such as virtual machines, web sites, and databases are always associated to a single subscription. If you belong to multiple directories, you can switch the current directory you are working in through the Directory + subscription button in the Azure portal header.
Every user who needs access to Azure resources needs an Azure user account. A user account contains all the information needed to authenticate the user during the sign-on process. Once authenticated, Azure AD builds an access token to authorize the user and determine what resources they can access and what they can do with those resources.
You use the Azure Active Directory dashboard in the Azure portal to work with user objects. Keep in mind that you can only work with a single directory at a time – but you can use the Directory + Subscription panel to switch directories.
Typically, Azure AD defines users in three ways:
- Cloud identities – These users exist only in Azure AD. Examples are administrator accounts and users that you manage yourself.
2. Directory-synchronized identities – These users exist in an on-premises Active Directory. A synchronization activity that occurs via Azure AD Connect brings these users into Azure.
3. Guest users – These users exist outside Azure. Examples are accounts from other cloud providers and Microsoft accounts such as an Xbox LIVE account. Their source is Invited user. This type of account is useful when external vendors or contractors need access to your Azure resources