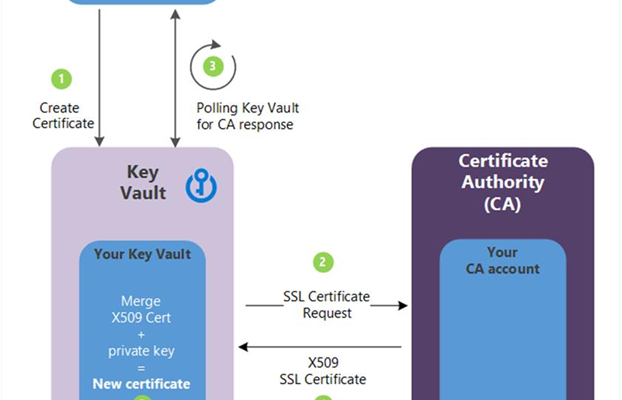
The certificates can be public and private Secure Sockets Layer (SSL)/Transport Layer Security (TLS) certificates signed by a certificate authority
The Cyber Security, Compliance & Cloud
Cyber Security | Digital Transformation | Cloud Computing

The certificates can be public and private Secure Sockets Layer (SSL)/Transport Layer Security (TLS) certificates signed by a certificate authority
FIDO2 is an open authentication standard hosted by the FIDO Alliance that consists of the W3C Web Authentication specification (WebAuthn
The System for Cross-domain Identity Management (SCIM) specification is designed to make managing user identities in cloud-based applications and services
Two-step verification is important for modern workplaces especially when employees are working remotely more and more, organisation boundaries are limitless,
Azure AD Connect sync is the successor of DirSync, Azure AD Sync, and Forefront Identity Manager with the Azure Active
Azure Active Directory is not designed to be the cloud version of Active Directory. It is not a domain controller