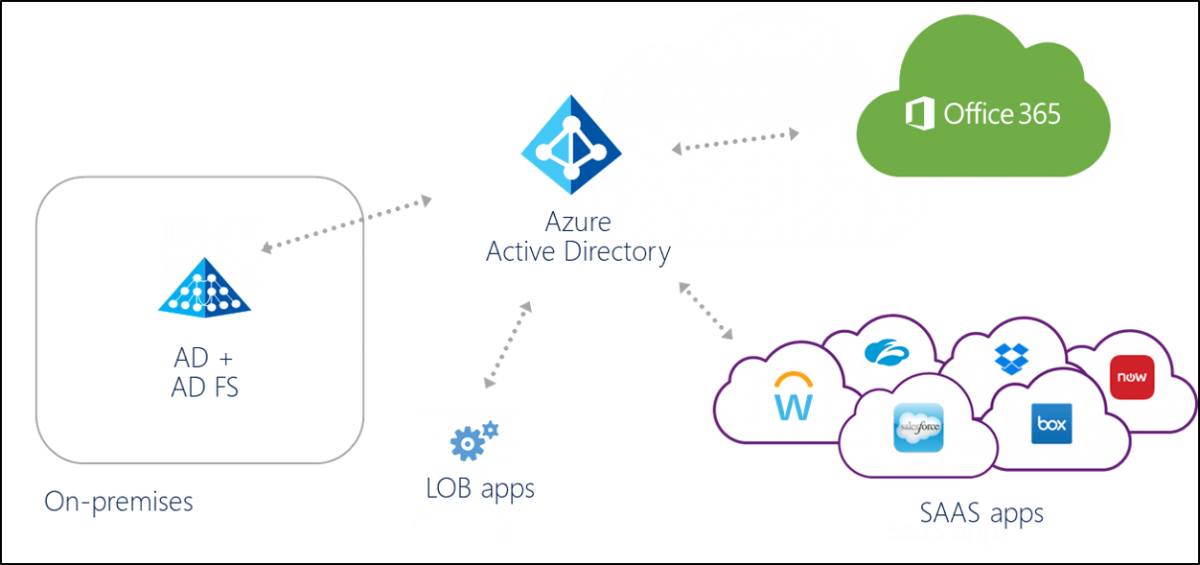
Azure Active Directory is not designed to be the cloud version of Active Directory. It is not a domain controller or a directory in the cloud that will provide the exact same capabilities with the AD. Actually, Azure Active Directory (Azure AD) is a multi-tenant, cloud-based directory, and identity management service.
That’s why there is no actual “migration” path from Active Directory to Azure Active Directory. You can synchronize your on-premises directories (Active Directory or other) to Azure Active Directory but not migrate your computer accounts, group policies, OU etc.
Some of Azure AD Features are:
- Application Management: Azure Active Directory (Azure AD) provides secure and seamless access to cloud and on-premises applications. Users can sign in once to access Office 365 and other business applications from Microsoft, thousands of software as a service (SaaS) applications, on-premises applications, and line of business (LOB) apps.
- Azure AD Authentication: Microsoft Azure Active Directory (Azure AD) includes features, like Azure Multi-Factor Authentication (Azure MFA) and Azure AD self-service password reset (SSPR), to help administrators protect their organizations and users with additional authentication methods.
Some organisation can take security one step further by adding their own customizations on top of the global banned password list in what Microsoft calls the custom banned password list
- Conditional Access: Conditional access is a capability of Azure Active Directory. With conditional access, you can implement automated access control decisions for accessing your cloud apps that are based on conditions. Here are ome common access concerns that conditional access can help you with:
Sign in Risk: A sign-in risk is an indicator of the likelihood (high, medium, or low).You can use the calculated sign-in risk level as condition in a conditional access policy.To use this condition, you need to have Azure Active Directory Identity Protection enabled..
Network Location: Define conditions based on where a connection was attempted.like from trusted locations and selected locations
Device Management: Azure AD identifies the platform by using information provided by the device, such as user agent. This condition is useful when a policy should apply only to an unmanaged device to provide additional session security.
Client Applications: By using the client apps condition, you can apply a policy to different types of applications. Examples are websites,services, mobile apps, and desktop applications.
- Identity Protection: Azure Active Directory Identity Protection is more than a monitoring and reporting tool. To protect your organization’s identities, you can configure risk-based policies that automatically respond to detected issues when a specified risk level has been reached. i.e Detect, Investigate and Conditional Access.
- Device Management: Device management is the foundation of a device based on conditional access. Through devices, your users are getting access to your corporate assets. To protect your corporate assets, as an IT administrator, you want to have control over these devices. This enables you to make sure that your users are accessing your resources from devices that meet your standards for security and compliance.
-
Single-Sign-On (SSO): users don’t see additional authentication prompts when accessing work resources. The SSO functionality is even when they are not connected to the domain network available.
-
Enterprise compliant roaming :Users don’t need to connect a Microsoft account (for example, Hotmail) to see settings across devices.
-
Access to Windows Store for Business: Your users can choose from an inventory of applications pre-selected by the organization.
-
Windows Hello support for secure and convenient access to work resources.
-
Restriction of access to apps from only devices that meet compliance policy.
-
Seamless access to on-premises resources when the device has line of sight to the on-premises domain controller.
For domain services, Azure offers a stand only service, called “Azure AD Domain Services ” that you could use to replicate your existing Active Directory implementation to the cloud. It is a stand-alone service that can offer domain services to your Azure VMs and your directory-aware applications if you decide to move them to Azure infrastructure services. But with no replication to any other on-premises or cloud (in a VM) domain controller.
If you want to migrate your domain controllers in the cloud to use them for the traditional task you could deploy domain controllers in Azure Virtual Machines and replicate via VPN.
So to conclude, if you would like to extend the reach of your identities to the cloud you can start by synchronizing your Active Directory to Azure AD.
Ref: Microsoft